Configuring SIP Interfaces
The SIP Interfaces table lets you configure up to
Each SIP Interface can be associated with only one SRD. As the SRD configuration entity represents your VoIP deployment SIP network (Layer 5), you need to associate your SIP Interfaces with a specific SRD in order to represent your Layer-3 networks. For most deployments (except multi-tenant deployments), your SRD represents your entire network and thus, only one SRD is required. The device provides a default SRD and in such scenarios where only a single SRD is required, your SIP Interfaces are automatically assigned to the default SRD. Therefore, there is no need to even handle SRD configuration entity.
Once configured, you can apply SIP Interfaces to calls, by assigning them to the following configuration entities in their respective tables:
| ■ | (Mandatory) Proxy Set to specify the SIP Interface for communication with the proxy server (i.e., IP Group). For more information, see Configuring Proxy Sets. |
| ■ | Intrusion Detection System (IDS) for applying the IDS policy to a specific SIP Interface. For more information, see Configuring IDS Policies. |
| ■ |
|
| ■ |
|
The SIP Interface can also be used for tag-based classification of incoming SIP dialogs if the SIP Interface is configured with a Call Setup Rule Set ID that determines the source tag. For more information, see Configuring Classification Based on Tags.
For more information on classification, see Configuring Classification Rules.
| ■ |
|
| ■ |
|
The device terminates active calls associated with a SIP Interface if you do one of the following:
| ● | Delete the associated SIP Interface. |
| ● | Edit any of the following fields of the associated SIP Interface: 'Application Type', 'UDP Port, 'TCP Port', 'TLS Port' or 'SRD' fields. |
| ● | Edit or delete a network interface |
The following procedure describes how to configure SIP interfaces through the Web interface. You can also configure it through ini file [SIPInterface] or CLI (configure voip > sip-interface).
| ➢ | To configure a SIP Interface: |
| 1. | Open the SIP Interfaces table (Setup menu > Signaling & Media tab > Core Entities folder > SIP Interfaces). |
| 2. | Click New; the following dialog box appears: |
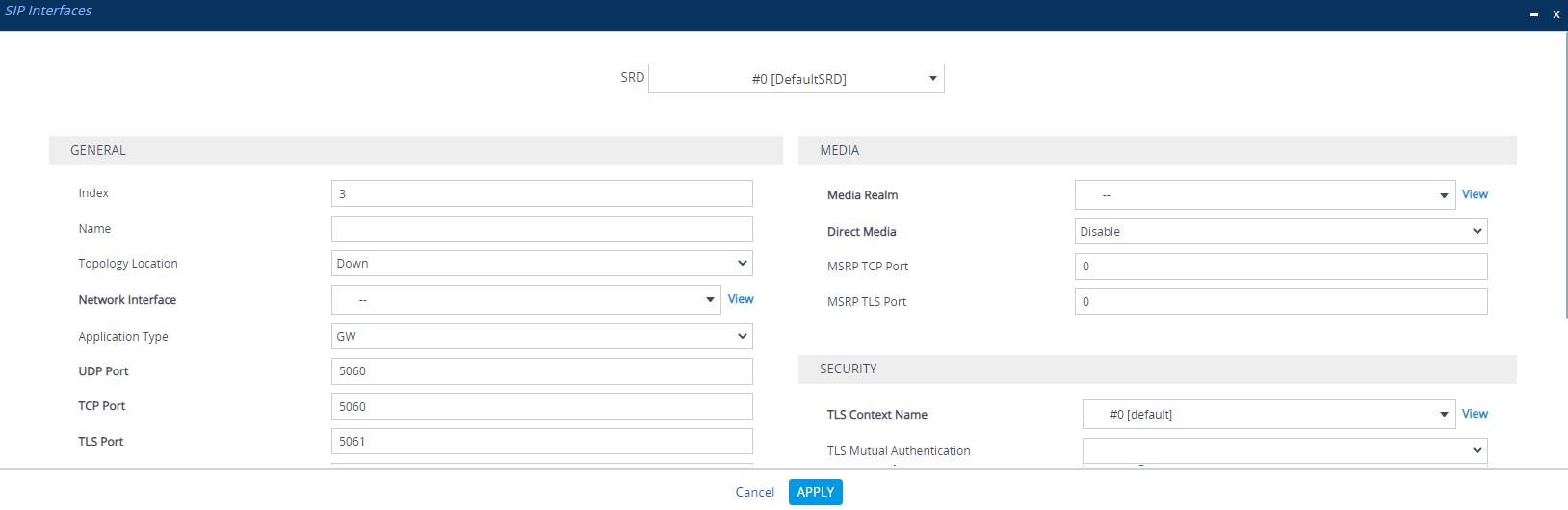
| 3. | Configure a SIP Interface according to the parameters described in the table below. |
| 4. | Click Apply. |
SIP Interfaces table Parameter Descriptions
|
Parameter |
Description |
|||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
'SRD' srd-name [SRDName] |
Assigns an SRD to the SIP Interface. If only one SRD is configured in the SRDs table, the SRD is assigned to the SIP Interface by default. If multiple SRDs are configured in the SRDs table, no value is defined and you must assign an SRD. To configure SRDs, see Configuring SRDs. Note:
|
|||||||||||||||||||||||||||||||||
|
General |
||||||||||||||||||||||||||||||||||
|
'Index' [Index] |
Defines an index for the new table row. Note: Each row must be configured with a unique index. |
|||||||||||||||||||||||||||||||||
|
'Name' interface-name [InterfaceName] |
Defines a descriptive name, which is used when associating the row in other tables. The valid value is a string of up to 40 characters. By default, if you do not configure a name, the device automatically assigns the name "<row index>" (e.g., "SIPInterface_1" when added to Index 1). Note:
|
|||||||||||||||||||||||||||||||||
|
'Topology Location' topology-location [TopologyLocation] |
Defines the display location of the SIP Interface in the Topology view in the Web interface.
For more information on the Topology view, see Building and Viewing SIP Entities in Topology View. |
|||||||||||||||||||||||||||||||||
|
'Network Interface' network-interface [NetworkInterface] |
Assigns an IP Interface to the SIP Interface. By default, no value is defined. To configure IP Interfaces, see Configuring IP Network Interfaces. Note:
|
|||||||||||||||||||||||||||||||||
|
'Application Type' application-type [ApplicationType] |
Defines the application for which the SIP Interface is used.
|
|||||||||||||||||||||||||||||||||
|
'UDP Port' udp-port [UDPPort] |
Defines the device's listening and source port for SIP signaling traffic over UDP. The valid range is 1 to 65534. The default is 5060. Note:
|
|||||||||||||||||||||||||||||||||
|
'TCP Port' tcp-port [TCPPort] |
Defines the device's listening port for SIP signaling traffic over TCP. The valid range is 1 to 65534. The default is 5060. Note:
|
|||||||||||||||||||||||||||||||||
|
'TLS Port' tls-port [TLSPort] |
Defines the device's listening port for SIP signaling traffic over TLS. The valid range is 1 to 65534. The default is 5061. Note:
|
|||||||||||||||||||||||||||||||||
|
'Additional UDP Ports' additional-udp-ports [AdditionalUDPPorts] |
Defines a port range for the device's local, listening and source ports for SIP signaling traffic over UDP. The parameter can be used for the following features:
The valid range is 1,025 to 65535. The range is configured using the syntax x-y, where x is the starting port and y the ending port of the range (e.g., 6000-7000). By default, the parameter is not configured. Note:
|
|||||||||||||||||||||||||||||||||
|
'Additional UDP Ports Mode' additional-udp-ports-mode [AdditionalUDPPortsMode] |
Enables the device to open sockets (ports) for signaling only when needed. The parameter applies to the Additional UDP Port feature with dynamic port allocation (see the 'Additional UDP Ports' parameter, above). This allows you to configure the additional UDP port range without having to make sure that the total number of configured ports are within the maximum, as defined by the device's License Key.
Note:
|
|||||||||||||||||||||||||||||||||
|
'Enable TCP Keepalive' tcp-keepalive-enable [TCPKeepaliveEnable] |
Enables the TCP Keep-Alive mechanism with the IP entity on this SIP Interface. TCP keep-alive can be used, for example, to keep a NAT entry open for clients located behind a NAT server, or simply to check that the connection to the IP entity is available.
Note: To configure TCP keepalive, use the following parameters: [TCPKeepAliveTime], [TCPKeepAliveInterval], and [TCPKeepAliveRetry]. |
|||||||||||||||||||||||||||||||||
|
'Used By Routing Server' used-by-routing-server [UsedByRoutingServer] |
Enables the SIP Interface to be used by a third-party routing server or ARM for call routing decisions.
For more information on the third-party routing server or ARM feature, see Centralized Third-Party Routing Server. |
|||||||||||||||||||||||||||||||||
|
'Pre-Parsing Manipulation Set' pre-parsing-man-set [PreParsingManSetName] |
Assigns a Pre-Parsing Manipulation Set to the SIP Interface. This lets you apply pre-parsing SIP message manipulation rules on any incoming SIP message received on this SIP Interface. By default, no Pre-Parsing Manipulation Set is assigned. To configure Pre-Parsing Manipulation Sets, see Configuring Pre-parsing Manipulation Rules. Note:
|
|||||||||||||||||||||||||||||||||
|
'CAC Profile' cac-profile [AdmissionProfile] |
Assigns a Call Admission Control Profile (CAC rules) to the SIP Interface. By default, no value is defined. To configure CAC Profiles, see Configuring Call Admission Control. |
|||||||||||||||||||||||||||||||||
|
Classification |
||||||||||||||||||||||||||||||||||
|
'Classification Failure Response Type' classification-fail-response-type [ClassificationFailureResponseType] |
Defines the SIP response code that the device sends if a received SIP request (OPTIONS, REGISTER, or INVITE) fails the SBC Classification process. The valid value can be a SIP response code from 400 through 699, or it can be set to 0 to not send any response at all. The default response code is 500 (Server Internal Error). This feature is important for preventing Denial of Service (DoS) attacks, typically initiated from the WAN. Malicious attackers can use SIP scanners to detect ports used by SIP devices. These scanners scan devices by sending UDP packets containing a SIP request to a range of specified IP addresses, listing those that return a valid SIP response. Once the scanner finds a device that supports SIP, it extracts information from the response and identifies the type of device (IP address and name) and can execute DoS attacks. A way to defend the device against such attacks is to not send a SIP reject response to these unclassified "calls" so that the attacker assumes that no device exists at such an IP address and port. Note:
|
|||||||||||||||||||||||||||||||||
|
'Pre Classification Manipulation Set ID' preclassification-manset [PreClassificationManipulationSet] |
Assigns a Message Manipulation Set ID to the SIP Interface. This lets you apply SIP message manipulation rules on incoming SIP initiating-dialog request messages (not in-dialog), received on this SIP Interface, prior to the Classification process. By default, no Message Manipulation Set ID is defined. To configure Message Manipulation rules, see Configuring SIP Message Manipulation. Note:
|
|||||||||||||||||||||||||||||||||
|
'Call Setup Rules Set ID' call-setup-rules-set-id [CallSetupRulesSetId] |
Assigns a Call Setup Rules Set ID to the SIP Interface. The Call Setup Rule is run before the Classification stage. By default, no Call Setup Rules Set ID is defined. To configure Call Setup Rules, see Configuring Call Setup Rules. Call Setup Rules can be used for Classification of incoming calls to IP Groups based on tags (source), as described in Configuring Classification Based on Tags. Note:
|
|||||||||||||||||||||||||||||||||
|
'Classify By Registration DB' classify-by-reg-db [ClassifyByRegDB] |
Enables classification to IP Groups of incoming SIP dialog-initiating requests (e.g., INVITE) by the device’s users registration database.
Note: The parameter is applicable only to the SBC application. |
|||||||||||||||||||||||||||||||||
|
Media |
||||||||||||||||||||||||||||||||||
|
'Media Realm' media-realm-name [MediaRealm] |
Assigns a Media Realm to the SIP Interface. By default, no value is defined. To configure Media Realms, see Configuring Media Realms. |
|||||||||||||||||||||||||||||||||
|
'Direct Media' sbc-direct-media [SBCDirectMedia] |
Enables direct media (RTP/SRTP) flow or media bypass (i.e., no Media Anchoring) between endpoints associated with the SIP Interface for SBC calls.
For more information on direct media, see Direct Media. Note:
The reason for the above is that in direct media, the device doesn't interfere in the SIP signaling such as manipulation of IP addresses, which is necessary for calls between LAN and WAN.
|
|||||||||||||||||||||||||||||||||
|
'MSRP TCP Port' msrp-tcp-port [MSRPTCPPort] |
Defines the listening TCP port for MSRP sessions. The valid range is 4000 to 32768. The default is 0. The port number is used in the SDP's 'a=path' line. For more information on MSRP, see Configuring Message Session Relay Protocol. Note: The port number must be unique for the SIP Interface (i.e., different to 'MSRP TLS Port', 'UDP Port', 'TCP Port' and 'TLS Port' parameters). |
|||||||||||||||||||||||||||||||||
|
'MSRP TLS Port' msrp-tls-port [MSRPTLSPort] |
Defines the listening TLS port for secured MSRP sessions (MSRPS). The valid range is 4000 to 32768. The default is 0. The port number is used in the SDP body's 'a=path' line. For more information on MSRP, see Configuring Message Session Relay Protocol. Note:
|
|||||||||||||||||||||||||||||||||
|
Security |
||||||||||||||||||||||||||||||||||
|
'TLS Context Name' tls-context-name [TLSContext] |
Assigns a TLS Context (TLS configuration) to the SIP Interface. The default TLS Context ("default" at Index 0) is assigned to the SIP Interface by default. Note:
|
|||||||||||||||||||||||||||||||||
|
'TLS Mutual Authentication' tls-mutual-auth [TLSMutualAuthentication] |
Enables TLS mutual authentication for the SIP Interface (when the device acts as a server).
By default, no value is defined and the [SIPSRequireClientCertificate] global parameter setting is applied. |
|||||||||||||||||||||||||||||||||
|
'Message Policy' message-policy-name [MessagePolicyName] |
Assigns a SIP message policy to the SIP interface. To configure SIP Message Policy rules, see Configuring SIP Message Policy Rules. |
|||||||||||||||||||||||||||||||||
|
'User Security Mode' block-un-reg-users [BlockUnRegUsers] |
Defines the blocking (reject) policy for incoming SIP dialog-initiating requests (e.g., INVITE messages) from registered and unregistered users belonging to the SIP Interface.
Note:
|
|||||||||||||||||||||||||||||||||
|
'Enable Un-Authenticated Registrations' enable-un-auth-registrs [EnableUnAuthenticatedRegistrations] |
Enables the device to accept REGISTER requests and register them in its registration database from new users that have not been authenticated by a proxy/registrar server (due to proxy down) and thus, re-routed to a User-type IP Group. In normal operation scenarios in which the proxy server is available, the device forwards the REGISTER request to the proxy and if authenticated by the proxy (i.e., device receives a success response), the device adds the user to its registration database. The routing to the proxy is according to the SBC IP-to-IP Routing table where the destination is the proxy’s IP Group. However, when the proxy is unavailable (e.g., due to network connectivity loss), the device can accept REGISTER requests from new users if a matching alternative routing rule exists in the SBC IP-to-IP Routing table where the destination is the user’s User-type IP Group (i.e., call survivability scenarios) and if the parameter is enabled.
Note:
|
|||||||||||||||||||||||||||||||||
|
'Max. Number of Registered Users' max-reg-users [MaxNumOfRegUsers] |
Defines the maximum number of users belonging to the SIP Interface that can register with the device. By default, no value is defined (i.e., the number of allowed user registrations is unlimited). Note: The parameter is applicable only to the SBC application. |
|||||||||||||||||||||||||||||||||